Database Audit Log: complete control over your data
In the past, we wrote about data security and ActivityInfo and we analyzed the precautions and actions we take to make sure that your data is always safe in the platform.
In this blog post we are presenting the brand-new Database Audit Log which has been designed to give to Database owners even more control over the information managed in their Databases.
Up to today data recovery was possible but you had to contact us to handle this. Using the Database Audit Log you can handle accidental data loss on your own. You can detect deleted Records and recover them in a single click.
In addition, by having a complete overview of the actions of your users you can detect early enough any potential disruptive user or malicious activity and take immediate action.
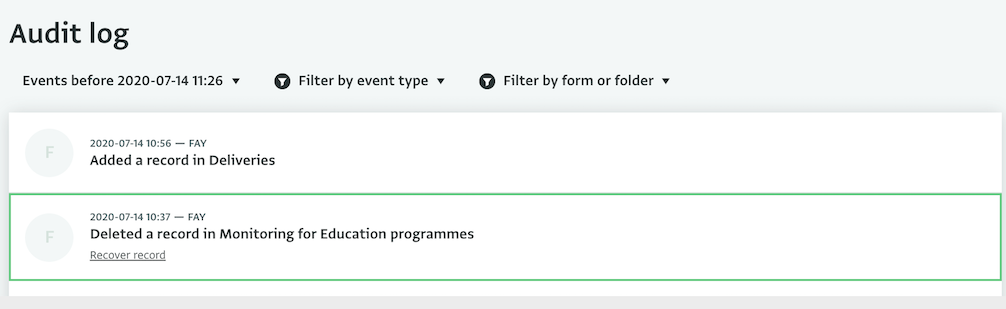
Recovering Data
With the Audit Log you can reduce the risk of data loss and handle such cases on your own, quickly and easily. You can find the deleted Records in a Form, Folder or in the entire Database and review which user deleted them and when. You can directly view and use the email of the user that deleted the Record so as to contact them, if necessary.
In case of a deleted Record, you can simply click on “Recover record” to restore the Record to the Database.
Protecting data against insider threats
An insider threat is a threat that comes from within an organization. Such threats could be people working in or cooperating with an organization such as employees, contractors or former employees who still have access to their account and more. Malicious insiders can be motivated by frustration with their employment situation, by fraud, or in some cases by political motives that conflict with the values of their organization.
In ActivityInfo, you can export a list of the users of your Databases along with their role and assigned resources to review it anytime. We recommend that you are always aware of the people who can access your Databases in ActivityInfo and that you take action when an individual leaves your organization in order to remove them from the system.
Best practices used for threats coming from the outside, such as using strong passwords, don’t work in the insider threat case as the individual already has access to the information via a legitimate account. However, having very refined control over what information each individual user can access and what they can do with it in combination with tools to detect malicious activity the moment it happens helps to mitigate the risk.
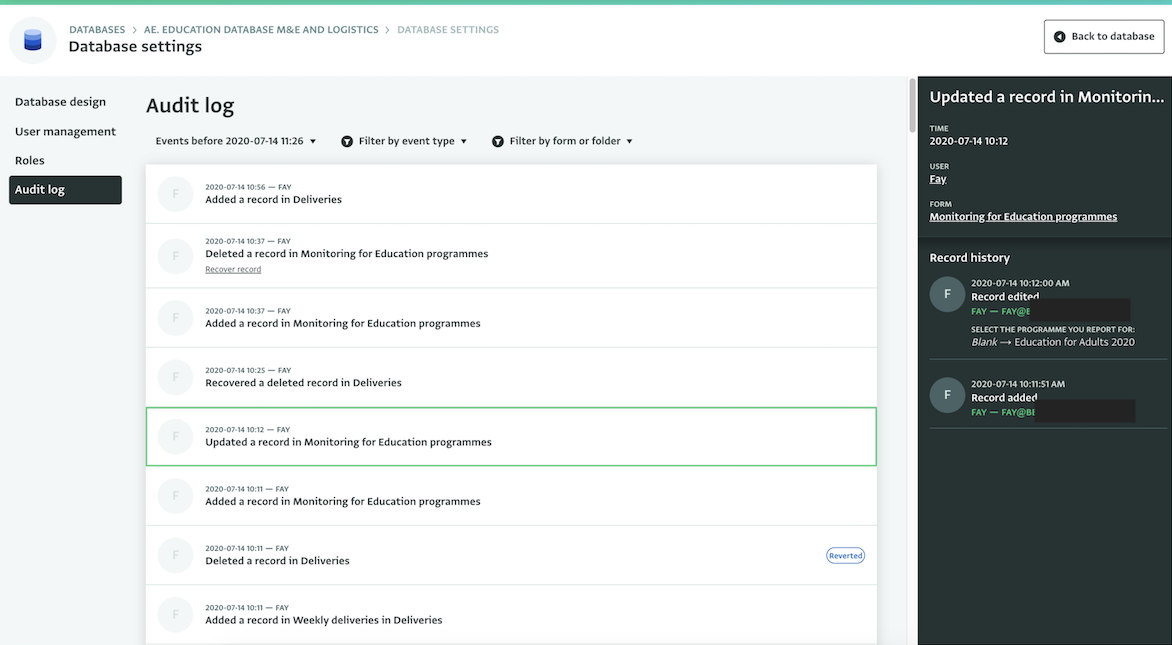
With the Database Audit Log you can have a complete overview of the events that took place in your Databases. You can view which users performed which actions and you can quickly detect any anomalies, unsolicited changes or record deletions so as to take immediate action.
By selecting an event you can view details about it such as the time of the event, the user who performed it and more. For example, you can select the event of an updated Record to understand which user updated the Record and view what the update was in detail. You can also navigate to the Table View of the Form where the Record belongs. Finally you can view and use the email of the user that performed the edit so as to contact them or revoke their access, if necessary.
Using the Database Audit Log
In the Database Audit Log you can review all events and changes that took place in your Database. The log presents a variety of events related to your Forms and Folders and gives you an overview of the users that applied the changes.
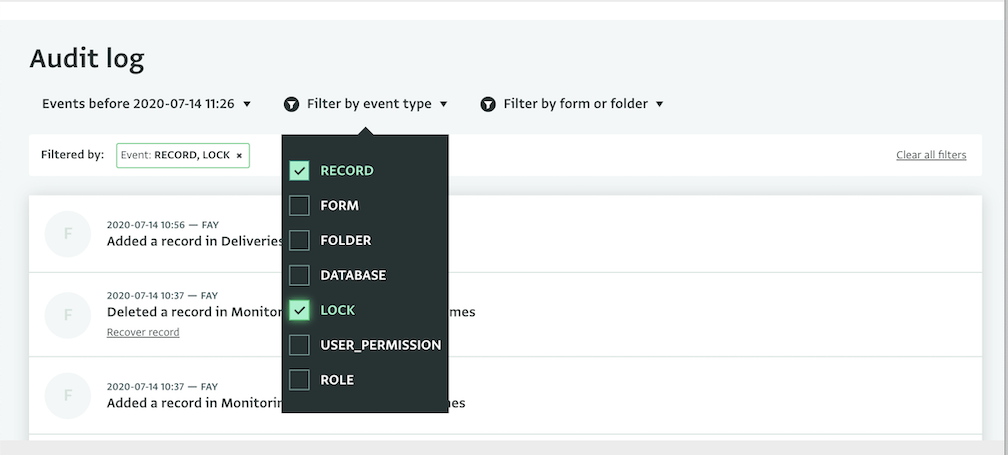
The types of events that you can review in the Database Audit Log include:
- Adding, updating or deleting Records
- Adding, updating, or deleting Folders, Locks, Roles
- Deleting or moving Forms or updating Form's visibility
- Adding or deleting users, or changing their permissions
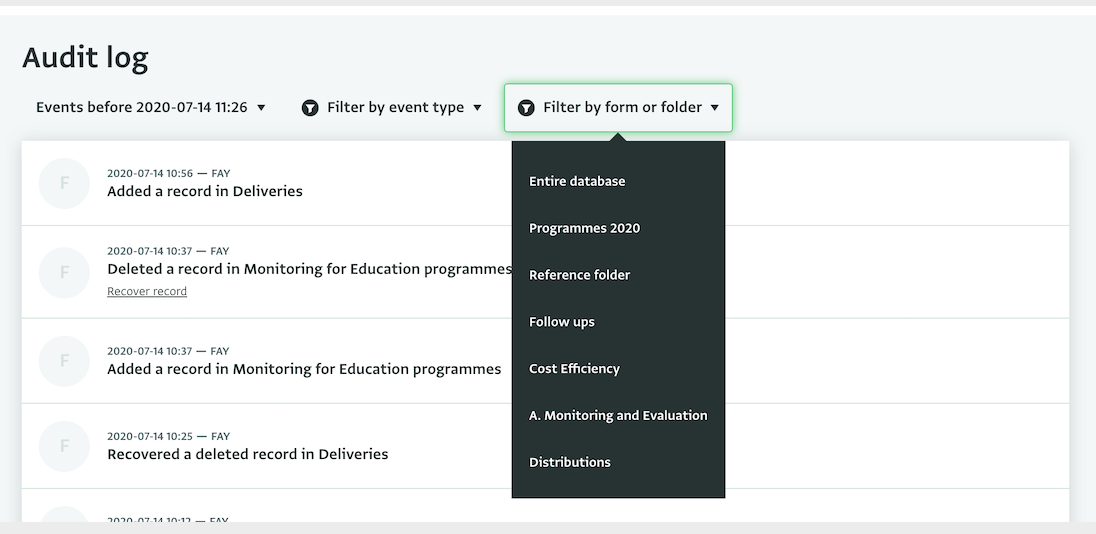
You can apply various filters to the Audit Log to find the event you need more easily. You can filter the logs based on your Forms or Folders or based on the type of the event. You can also set a date and browse events before that date.
What do you think about the Database Audit Log? Will this be useful for you? Make sure to read more about it in our User Manual!